Most File Systems have unique ways for doing things, but also many things in common. On a Macintosh you might have some extended attributes, or that pesky hidden .DS_Store file no one really knows why it’s there. On Windows you may find a hidden thumbs.db file throwing off your file count. Hidden files are everywhere. Many have a real purpose, and that purpose may be insignificant or important in finding or giving context to other files.
While processing a collection from a USB drive the other day, I came across a few files I hadn’t seen before. They were hidden files nestled in with a few folders of PDF’s. They have a unique name, so I figured it would be easy to find some documentation on them on the web. Turns out, there is very little.
-rwx------@ 1 tyler staff 235 Aug 22 00:04 XNAME.CRS
-rwx------@ 1 tyler staff 235 Aug 22 00:04 XNAME.LIB
The files were only a couple years old, so I figured there had to be some modern software which created them. A look inside the files with a hex editor didn’t provide much information.
hexdump -C XNAME.LIB
00000000 22 80 21 36 00 00 00 00 00 00 00 00 00 00 00 00 |".!6............|
00000010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00000090 00 00 00 00 00 00 4c 3c 55 6e 61 73 73 69 67 6e |......L<Unassign|
000000a0 65 64 3e 00 00 00 00 00 00 00 00 00 00 00 00 00 |ed>.............|
000000b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
I was about to give up since there wasn’t much data and since they were hidden files, I assumed they were probably just some cached files with little value. But wanting to learn more I did some more digging and at first thought they might have something to do with DropBox, as a user said they just showed up one day, but later found they probably were created by some Document Management software known as Worldox. I found a support page claiming these two files are part of a database.
XNAME.LIB Contains document numbers (DOS names), extended names, and file security information.
XNAME.CRS Contains custom profile field and version control information.
There is a key term in the definition of XNAME.LIB, “extended names”. I was curious what that meant and found Worldox has been around awhile. The World Software Corporation has been around since 1988 and Worldox was released in 1993, but before that it specialized in an interesting DOS software package called “Extend-A-Name” or “Extend-A-File”. The name gives away its purpose, it literally extends the name of the limited 8 Characters you could use in DOS. I can remember trying to decide on a filename that would accurately describe my file so I knew what it was later on. 8 characters is not enough to explain the content of a file, especially if you have hundreds or thousands of file to manage.

Extend-a-file was software which bonded with another piece of software like WordPerfect and loaded itself in memory. Then when you went to create a file or locate a file within WordPerfect, Extend-a-File would take over and allow you to create a file with a traditional 8 Character name, but also a name much longer.

This extended name allowed you to describe the files content with much more detail. Making it also very easy to find previous documents.
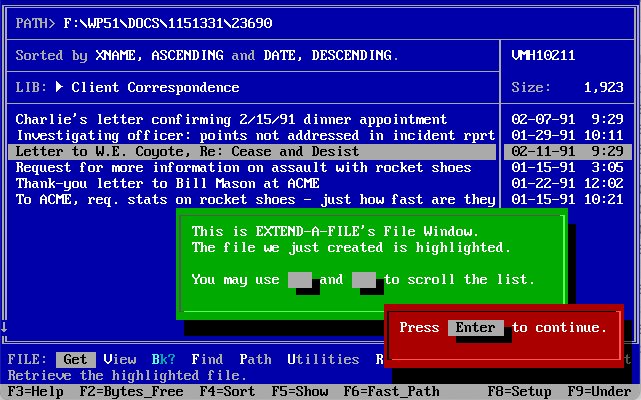
Pretty slick, this software really would make a big difference to managing a large amount of files in the old DOS days. Ok, it adds extended names, but where is this information stored? That is where the XNAME files come into play.
hexdump -C XNAME.LIB | head
00000000 6d 92 15 59 47 47 15 00 00 00 00 00 00 00 00 00 |m..YGG..........|
00000010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00000090 00 00 00 00 00 00 4c 10 20 4d 41 53 54 45 52 20 |......L. MASTER |
000000a0 4c 49 42 52 41 52 59 20 2d 20 41 6c 6c 20 46 69 |LIBRARY - All Fi|
000000b0 6c 65 73 20 4c 69 73 74 65 64 00 20 64 72 69 76 |les Listed. driv|
000000c0 65 20 43 20 00 58 4e 50 4c 55 53 2e 24 24 24 00 |e C .XNPLUS.$$$.|
000000d0 fd 05 fe 49 6e 73 75 66 66 69 63 69 65 6e 74 20 |...Insufficient |
000000e0 64 69 73 6b 20 73 70 61 63 65 20 46 54 68 69 73 |disk space FThis|
000000f0 20 69 73 20 61 20 74 65 73 74 20 6f 66 20 58 4e | is a test of XN|
00000100 41 4d 45 20 20 20 20 20 20 20 20 20 20 20 20 20 |AME |
00000110 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
00000120 20 20 20 20 20 20 20 20 00 56 44 53 30 30 30 30 | .VDS0000|
00000130 2e 44 4f 43 00 00 96 00 56 44 53 00 00 00 00 4f |.DOC....VDS....O|
00000140 55 30 30 30 30 30 30 0a 09 1d 00 02 00 00 00 00 |U000000.........|
00000150 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
This XNAME.LIB was generated by a running copy of XNPLUS circa 1990, bonded with a copy of DisplayWrite 4. It adds much more information within the “Library”.
So it seems this method of storing the extended filenames and other metadata started in the Extend-a-File software and has been brought along and used in modern versions of the Worldox Document Management software. Much of its purpose to extend an 8 character filename to around 60 character is no longer needed as most systems now allow for filenames with at least 256 characters. I imagine there is more the software can add to these files, but found that the samples I have really don’t have any information in them at all. The Worldox software seems to be marketed toward law firms and others who have a lot of documents to manage, but I have been unable to find a way to play with the software to see what can be embedded within the XNAME.LIB files.
There is also some discussion out there about wether to backup these two hidden files and what might happen if they are lost. Regardless, you may want to think twice before tossing them as I almost did. They could contain valuable information needed to give context.
I am not sure it is possible to have a good signature for identification of these files. The samples I have and others I found online, here, here, here, and here, just don’t have much data within them. In fact they are all exactly 235 bytes. The only consistent byte within them and the samples I generated from XNPLUS is “4C” at offset 150, but everything else seems arbitrary. Here is a sample I generated from XNPLUS if you want to take a closer look.